At the time, when you are planning for a new website or application for your business, the chances of using PHP application is higher than any other frameworks.
And the reason is pretty clear – its way more dynamic than other platforms or most of it.
Today most of the websites are equipped with an impeccable PHP framework. Therefore it becomes much more likely to prevent data breaches. Also, most of the attacks were made with Buffer Overflow, Remote File inclusion, and XSS has targeted the most vulnerable points for the websites. But, if you are Thinking of How to secure php websites?
Never miss an update from us. Join 10,000+ marketers and leaders.
Thus to avoid cyber threats, most of the entrepreneurs depend on the websites that are developed with all the PHP Website Security measures.
PHP is highly popular because of its features to maximize the performance and has ability to develop complex dynamic websites, faster.

The below are some of the reason why ‘PHP’is becoming or has become one of the most preferred development platforms by developers, agencies and tech giants;
- PHP is damn-User Friendly! When put into comparison among other scripting languages, PHP is the most user-friendly platform…
- PHP is Flexible! …
- PHP is Dynamic! …
- PHP is Low Cost! …
- PHP Hast Fast Data Processing! …
- PHP is Open Source! …
- PHP is High Performing! …
- PHP is Able to Cross Platforms!
According to w3techs survey, 83% websites are using PHP as server side programing language.
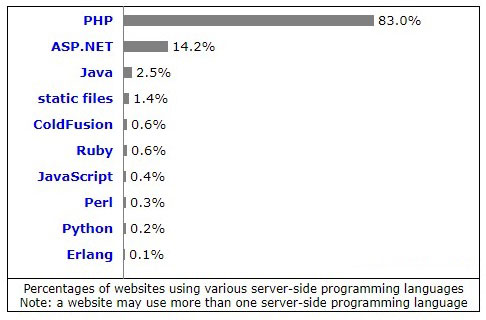
(Source: w3techs)
Industry wise the use of PHP frame work also high compared to others,
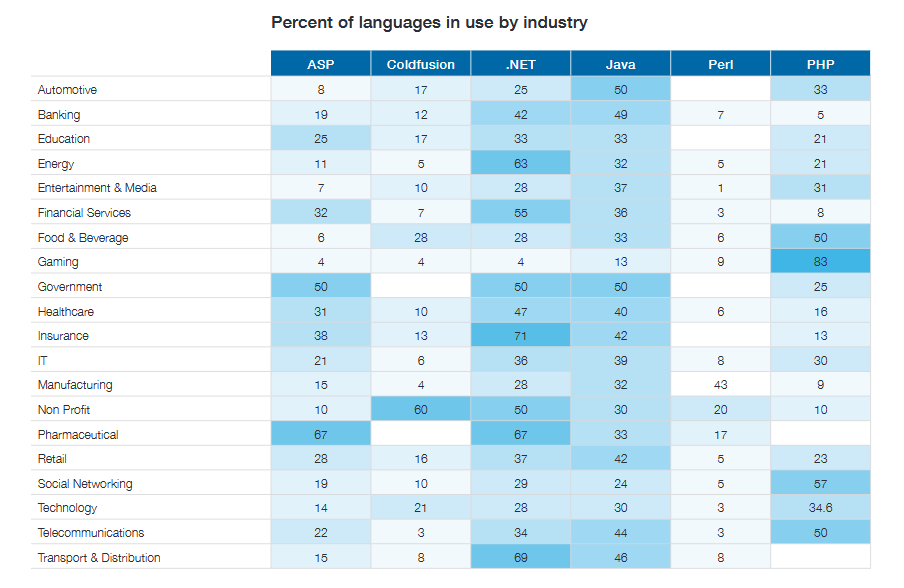
(Source: WhiteHat Security)
I love it. I think it is a great step in the development of the language, PHP is a seriously mature language now, which can easily compete with other languages. And it’s being used for highly scalable and business-critical applications.
– ByStefan Koopmanschap, cofounder of PHPBenelux
So, telling the tale above – What’s the most important threat to PHP as a technology?
That’s correct – SECURITY
When it comes to security of application, you need to maintain some additional security codes, to keep your application or website secure from hackers. Because PHP is not 100% bulletproof and your PHP developer must understood the value of security and should take necessary steps to make it secure.
Every language has some security vulnerabilities in various aspects. Here I will share the techniques to minimize security vulnerabilities in PHP Application Development but before that lets have a look at the major security weaknesses,
- Input data validation
- Cross-Site Request Forgery (CSRF)
- Protection against XSS attacks
- Proper error handling
- SQL Injection (SQLi)
- Remote and Local File Inclusion (RFI and LFI)
- Remote Code Execution (RCE)
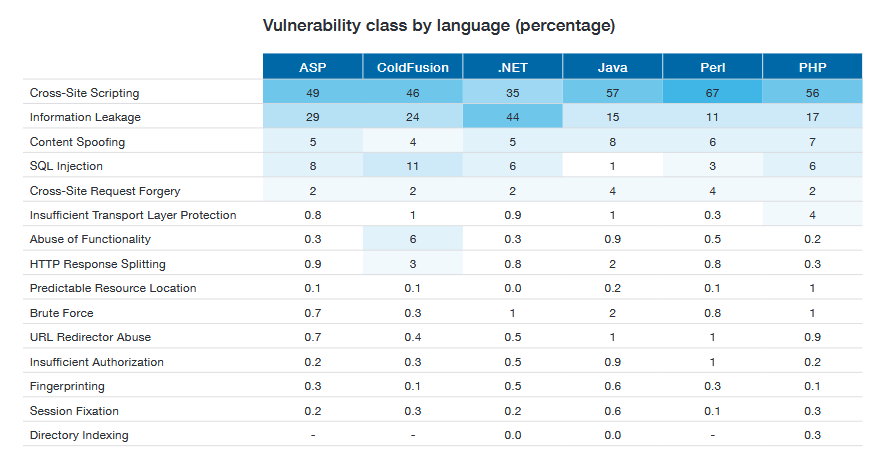
(Source: WhiteHat Security)
Let’s move to the main topic. Every language has remediation for their security vulnerabilities. Have a look at the remediation percentages of various languages by vulnerabilities class.
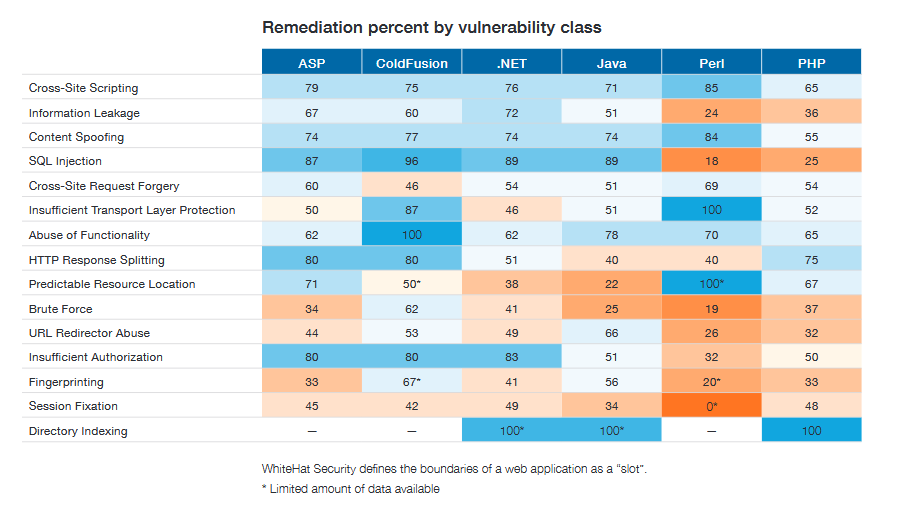
(Source: WhiteHat Security)
Contents
Techniques To Minimize Security Vulnerabilities:
Here we will share the top important techniques to minimise the security vulnerabilities of PHP,
1. Input Data Validation:
You should protect your application against bad inputs while designing application. Do not trust your users and theirs inputs. You have developed your app with good intent but thereare users who will try to attack your app through wrong inputs. So you should use filter to validate the incoming data to keep your application secure.
You need to validate your PHP code always, because user may turn off the JavaScript in their browser and your app will not validate the user. Your PHP developer must know about the type of input data for validation.
2.Cross-Site Request Forgery (CSRF)
Cross Site Request Forgery (CSRF) isa trick to hack app information. If your application is badly coded, then at that situation – the hacker hacks the information with GET request without the knowledge of the user. Through GET request, a single page can be accessed multiple times without any side effects. GET request is only used for accessing the information but not for any transactions.
3.Protection Against XSS Attacks
Cross-site scripting (XSS attack) is the code injection that routes them to vulnerable web pages which shows the non-validate input data in the browser and may redirect the user to other website. When user submits data in the input field which contains malicious JavaScript code, the data gets stored in the server database when the malicious JavaScript code runs, that takes the user to a different page.
4.Proper Error Handling
It’s always good to know the errors at the time of development – working on a proactive state helps to build a much robust application over PHP.
But if the errors occur at the exact moment when you’re about to launch your application to live (or a part of it as a module) then it does make your app vulnerable for injections and attacks.
So it’s alwaysbetter to configure your server differently for development and for production.
You can also set custom error handler.
5.SQL Injection (SQLi)
Most of the web developers are not security experts and skip the basic validations that will provide severe security holes.
The SQL Injections are a technique where an attacker will develop or alter the existing SQL commands to expose or override any data.
SQL injection attacks happens when data goes unverified, and the application doesn’t escape characters used in SQLstrings such as single quotes (‘) or double quotes (“).To perform your database queries, you should be using PDO with parameterized queries and prepared statements, this way you can prevent SQL injection attacks.
Below is an example on how PHP application let the user change the password by using the query developed in this way.
$query = “UPDATE users SET password=’$password‘ WHERE user_id=’$user_id‘”;
Since the `$password` variable isn’t unique before being developed in the query. So, when an attacker will easily make themselves an administrator by inputting something like this into the password field on the web form:
passw0rd‘, admin=’yes
If there was an `admin` field on the `users` table, it would be set to `yes` and that user would have admin privileges.
The best way to avoid these kinds of attacks is to check properly and then provide a password, all user inputs by ensuring that they are a specific data type (e.g. a number rather than a text or a combination) and check whether they there is any kind of malicious activity taking place.
6.Remote And Local File Inclusion (RFI and LFI)
Remote file inclusion happens when remote file gets included with your application, because remote files are not trusted.
It could have been maliciously modified to contain code you don’t want them running in your application.
Fixing this attack is very simple. You need to go to your php.ini and check the settings on these flags.
- allow_url_fopen – indicates whether external files can be included. The default is to set this to ‘on’ but you want to turn this off.
- allow_url_include – indicates whether the include(), require(), include_once(), and require_once() functions can reference remote files. The default sets this off, and setting allow_url_fopen off forces this off too.
7.Front-End Test
Font-end-testing helps in finding security vulnerabilities in your application code, rather always checking the code of your backend.
In your application form you can do vulnerability tests against XXS attacks, SQL injections, and others to find the frontend attack which are not easy to find out sometimes.
8.Unit Testing
For permission and restricted functionality – unit testing is the best option to find security vulnerabilities.
Unit testing is the method to test certain functionality of code snippet which allows you to easily know whether the functionality is working or not.
Without proper unit testing you cannot check the permission and restriction functionality of your application.
9. Update Your PHP Version Regularly:
As of July 9, 2020, a stable release for PHP version was established i.e Version 7.4.8. It is necessary that you update your version regularly. The newer version contains patches for many known security issues.
If you fail to update the PHP version to the latest, the hackers will exploit those known PHP security vulnerabilities with many older releases.
10.Testing Your Code As You Develop
Instead of testing your whole work after the development. Test your app as you develop as a on-going process.
I’ve worked with the team at Andolasoft on multiple websites. They are professional, responsive, & easy to work with. I’ve had great experiences & would recommend their services to anyone.
Ruthie Miller, Sr. Mktg. Specialist
Salesforce, Houston, Texas

This will give opportunity to find out the bugs or security vulnerabilities within the development process. If you will test the entire code, you may not detect the exact fault and conditional statement because you missed another error that you could have if you would have tested while you develop the code.
Conclusion:
In the end, by keeping this information in mind, you can develop your applications. You need to be sure that your application is secure to a larger extent.
Keeping the above things in mind, if you develop your app accordingly, you can make your app secure to a great extent.
It’s up to your application developer to make you aware every moment – how much secure is your app and how much security you need to maintain to save your app from attack.
Still looking some help on PHP application development then, take the advantages of Andolasoft PHP Development Services and discuss with our experienced PHP Experts.
Share your comments and suggestion on PHP technology below, we would be happy to assist you.